“If you pay a ransom, will you get your files back?” It’s a ubiquitous question that the majority of security blogs and vendor surveys fail to answer correctly. A quick search online will yield a dozen contradictory statistics. Why is this such a difficult question to answer? The truth is outcome statistics vary dramatically from case to case, and broad averages are useless for making real time, critical decisions.
Most people assume the cause of ransomware-related data loss is due to threat actors deliberately stealing the ransom money and not providing the decryption keys. This is actually not true. Data loss usually stems from coding flaws sloppily written into the ransomware itself. These flaws come in lots of different shapes and sizes, but a common mistake involves the encryptor scrambling up the bytes of the file and failing to save the necessary keys into elements of the file that allow for decryption, making recovery impossible even with the correct decryption key.
Why Data Isn’t Recovered
Here’s how the encryption process is supposed to work: when the ransomware binary is executed by the threat actor, it creates a fast, one-time “symmetric” key for each unique file and uses that key to encrypt the file. Symmetric keys are used because they can encrypt large files quickly. Once the file is encrypted, the malware then encrypts that small, one-time key with the attacker’s public key and stores it at the end of the file — along with a recognizable marker and some basic metadata — in a section called the footer. As long as that footer is present and correct, the attacker’s private key can decrypt the one-time key, and that key can then be used to restore the file to its original format.
But if the footer is missing or damaged, that one-time key is effectively gone — and the file can never be recovered, even if the victim pays for a decryption tool.
Where Obscura Ransomware Breaks Data
A newly identified ransomware variant, Obscura, contains exactly this flaw. When it encrypts large files, it fails to write the encrypted temporary key to the file’s footer. For files over 1GB, that footer is never created at all — which means the key needed for decryption is lost. These files are permanently unrecoverable.
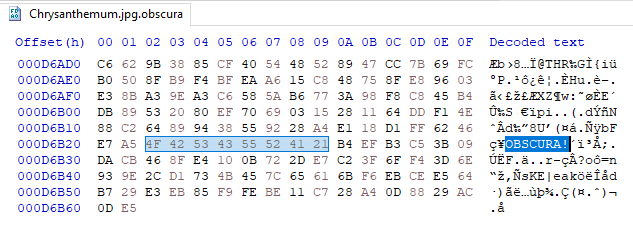
Here’s a sample of a small encrypted file. Note the filemarker “OBSCURA!” and the encrypted key saved to the end of the file.
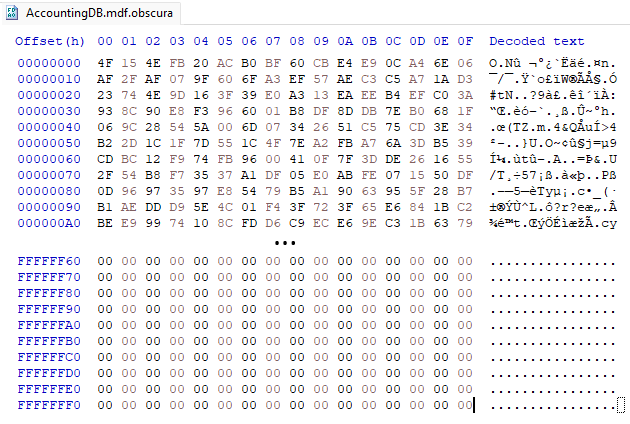
Here’s a large encrypted file. Note there is no filemarker or footer. (The footer is not present anywhere in the file.)
This flaw has major implications for victims, particularly when relying on “proof of life” tests when negotiating with threat actors. These tests usually involve sending a small encrypted file to the threat actor for decryption. The problem is that these samples almost never include large files, and large files are the most likely to be damaged by flaws in the ransomware code. Without deep insight into a ransomware family’s behavior, victims don’t even know which file sizes or categories they should test. In Obscura’s case, unless you send a file over 1GB, you will never discover that those files are handled differently — or that they are unrecoverable by design.
Recon Reveals Flaws in Obscura Ransomware
Coveware by Veeam’s proprietary tool, Recon, closes this visibility gap. Recon scans encrypted files at scale and checks for the presence of valid file markers, encrypted keys, and other metadata required for successful decryption. It can determine which files are properly encrypted, which are damaged or malformed, and which files were never encrypted at all.
Running Recon across all encrypted data can immediately identify files that are permanently corrupted, including common failure modes that plague large files: missing footers, incomplete writes, crashes during encryption, and integer-size errors from ransomware that was never tested against multi-gigabyte data. If the only irreplaceable data a victim needs falls into one of these failure categories, there is no justification for paying a ransom.
Below is a screenshot of what the Recon tool returns on a sample Obscura-encrypted files over 1GB in size.
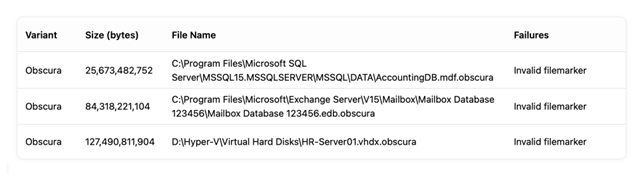
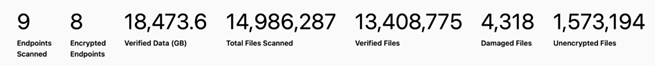
Note that Recon has found the missing footer and noted it as an invalid file marker. Recon is also able to summarize the total volume of files scanned, and the proportion that is verified as properly encrypted, damaged, and unencrypted. Coveware clients are given access to a portal that allows them to drill deeper into these results and view each schedule, down to the file level.
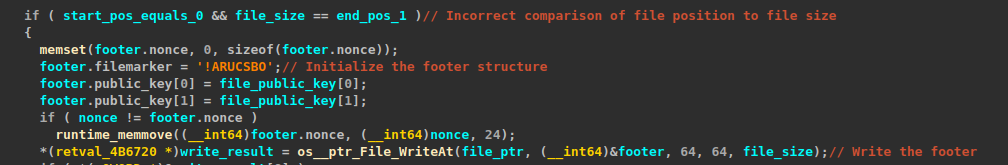
Reverse-engineering Obscura’s code confirms the issue: the malware only writes its footer if the file pointer reaches the physical end of the file.
Organizations need clear, actionable insight into what data can and cannot be recovered long before ransom negotiations begin. Coveware by Veeam’s Recon tool provides that visibility. Recon performs a technical evaluation of encrypted files at scale, allowing organizations to quickly determine:
- Which files were actually encrypted and which remain untouched
- Which files contain valid markers, keys, and metadata required for decryption
- Which files are already unrecoverable due to ransomware flaws — such as large files missing footers in Obscura’s case
Technical Validation is Non-Negotiable
Because Recon is informed by Coveware by Veeam’s ongoing reverse engineering of ransomware variants, it understands how different file categories should behave, which encryption modes each variant uses, and where corruption is most likely to appear. That insight is what makes Recon’s validation meaningful rather than superficial. This level of clarity allows victims to:
- Make informed decisions about ransom negotiations, backed by evidence instead of attacker assurances
- Set realistic, data-driven expectations for executives and incident response teams
- Direct recovery efforts toward backups or rebuilds, rather than spending time — or money — on data that cannot be saved
Obscura’s flaw reinforces a simple truth: organizations cannot rely on “honest criminals” to guarantee data recovery. Technical validation is not negotiable. Many victims hesitate to admit they were ransomed, and many still assume that paying will restore their data — but Obscura shows how dangerous that assumption is. This variant destroys large files outright, with no possibility of recovery. Raising awareness matters, because without it, victims may unknowingly pay for data that is already gone.
The Broad Reality
Tools like Recon allow organizations to independently verify the true state of their data before making decisions that cannot be undone. Recon can reveal corruption that proof-of-life tests will never catch, especially in cases like Obscura where large files — often the most critical files — are the ones most likely to be damaged.
At the same time, organizations need to understand the broader reality: threat actors watch for write-ups like this. They actively read technical analyses, study incident response workflows, and update their code when flaws or bugs are exposed. That ongoing back-and-forth is precisely why reliable, repeatable, variant-specific validation is essential — not one-off tests, not assumptions, and not attacker promises.
Key takeaways for organizations:
- Invest in incident response planning and technical validation tools before an incident occurs — not after.
- After a ransomware attack, thoroughly evaluate encrypted files to understand actual recovery options.
- Use independent, variant-aware analysis to guide ransom decisions — never rely on proof-of-life tests, attacker promises, or outdated marketing statistics
The post Obscura Ransomware: A Case Study in Ransomware Data Loss appeared first on Veeam Software Official Blog.
from Veeam Software Official Blog https://ift.tt/B7nE5Uj
Share this content:
