Key takeaways:
- Supply chain cyber risk is escalating attackers exploit vendor and third‑party weaknesses to gain access to critical systems.
- Visibility and verification are essential: you can’t protect what you can’t see, and blind trust in suppliers leaves gaps.
- Resilience is now a business imperative: it’s no longer enough to prevent breaches; you must recover fast when they happen.
- Data resilience is the new standard: the ability to protect, detect, and recover from any disruption, anywhere your data lives.
- A secure supply chain protects your brand, compliance standing, and customer trust: and positions your business to thrive despite disruption.
The modern supply chain has become more than just about moving goods or delivering services. It’s a complex, interconnected web of vendors, partners, platforms, and infrastructure. Every link in that chain is a potential doorway for cybercriminals.
We’ve seen it in high‑profile breaches: attackers bypass well‑secured organizations by targeting a smaller, less‑protected supplier. Once inside, they can move laterally, disrupt operations, and exfiltrate sensitive data. Supply chain attacks are among the fastest‑growing categories of cyber incidents, and they’re increasingly sophisticated.
That’s why supply chain risk management (SCRM) has evolved from a procurement checklist to a core cybersecurity discipline. It’s about knowing your dependencies, assessing their security posture, and having a plan to keep your business running, even if a critical vendor is compromised.
At Veeam, we call this Cyber Resilience, the ability to protect, detect, and recover from threats, disasters, and incidents, anywhere your data lives. It’s the mindset and capability that turns supply chain risk from a constant worry into a manageable, recoverable challenge.
In this blog, we’ll explore how modern SCRM works, the risks to watch for, and how Veeam helps you build a resilient, secure supply chain.
What is Supply Chain Risk Management?
Supply Chain Risk Management is the practice of identifying, assessing, and mitigating the risks that come from your network of suppliers, partners, and service providers. In today’s digital economy, it includes all digital assets, the software, cloud services, and data flows, as well as infrastructure, that keep your business running.
Every organization relies on a mix of third‑party vendors, from cloud hosting providers to software developers to hardware manufacturers. Each connection introduces potential vulnerabilities. If a supplier is compromised, attackers can use that access to infiltrate your systems, disrupt operations, or steal sensitive information.
Modern SCRM goes beyond contracts and compliance checks. It’s a continuous process that involves:
- Visibility: Knowing every vendor, service, and system that touches your environment.
- Verification: Assessing their security posture and ensuring they meet your standards.
- Contingency planning: Having clear, tested recovery paths if a vendor is compromised.
- Ongoing monitoring: Watching for changes in vendor risk profiles over time.
When done right, SCRM doesn’t just protect against cyberattacks, it also safeguards your brand reputation, helps meet regulatory requirements, and maintain customer trust. It’s the foundation for resilient operations in a world where risk can come from anywhere in your supply chain.
Too many organizations still treat SCRM as a “procurement problem” rather than a cyber resilience strategy. The reality is, it’s both, and your security and operations teams need to work together to manage it.
Why Supply Chain Risk Management Matters in Today’s Threat Landscape
Cybercriminals no longer need to attack you directly. They can target a weaker link in your supply chain and use it as a backdoor into your systems. This tactic is fast, effective, and increasingly common.
Recent breaches have shown that even the most well‑protected enterprises can be compromised through a trusted third‑party vendor. Once attackers gain that foothold, they can move laterally, install ransomware, or exfiltrate sensitive data, and often undetected for weeks.
What’s Changed?
There were three big shifts making supply chain risk harder to manage:
- Digital transformation has expanded the attack surface. Hybrid and multicloud environments mean more vendors, more integrations, and more potential entry points.
- Threat actors are targeting software creation and releasing mechanisms. Compromising a supplier’s code or distribution pipeline can give them access to thousands of downstream customers at once.
- Regulations are tightening. Frameworks like NIS2 and DORA now require organizations to demonstrate resilience, not just prevention, across their supply chains.
The Business Impact
A successful supply chain attack can cause:
- Operational downtime: halting critical services or production.
- Data loss or theft: including customer records, intellectual property, and financial information.
- Regulatory penalties: for failing to secure third‑party access or protect sensitive data.
- Reputation damage: eroding customer trust and market confidence.
Why it’s Urgent to Act Now
According to recent Veeam ransomware research, attackers often aim to compromise backup repositories. This makes resilient, secure backups a critical part of any supply chain risk strategy.
This is why modern SCRM must be proactive, continuous, and integrated with your overall cyber resilience plan. It’s not about if an incident will happen, it’s about how prepared you are to detect it, contain it, and recover without missing a beat.
Supply chain risk isn’t just an IT problem. It’s a business continuity problem. The organizations that survive are those that can recover faster than their competitors.
Common Supply Chain Risks Organizations Face
Your supply chain is only as strong as its weakest link. And in a complex, interconnected ecosystem, there are a lot of potential weak links. That risk can come from any stage of the vendor relationship, whether it’s a small SaaS provider or a major cloud platform.
Here are the most common supply chain risks threatening organizations today:
1. Third-Party Data Breaches
Vendors often store or process sensitive information, from customer data to proprietary designs. If they’re breached, your data could be exposed, even if your own systems are secure.
Example: A payroll provider suffers a cyberattack, leaking employee financial data and triggering compliance investigations for every client they serve.
2. Compromised Software Updates
Attackers inject malicious code into a supplier’s software update, which is then distributed to all customers. This tactic can bypass traditional defences because updates are usually trusted implicitly.
Example: A widely used IT management tool releases an update embedded with malware, giving hackers remote access to thousands of networks.
3. Cloud Service Vulnerabilities
Hybrid and multicloud strategies bring speed and flexibility but also add complexity. Misconfigurations, weak access controls, or vulnerabilities in a cloud provider’s environment can put your workloads at risk.
Example: A misconfigured storage bucket at a third-party cloud partner exposes critical intellectual property.
4. Vendor Operational Failures
Not all risks come from malicious actors. A vendor’s outage, bankruptcy, or business disruption can cascade into your operations, causing downtime or missed service levels.
Example: A niche supplier of a critical component shuts down unexpectedly, halting your ability to deliver your product on time.
5. Regulatory Non-Compliance
If a supplier fails to comply with industry regulations, you may still be held accountable, especially in highly regulated sectors like finance, healthcare, and energy.
Example: A subcontractor mishandles EU customer data, leading to GDPR fines for your organization.
These risks share one thing: they’re often outside your direct control. That’s why the need for visibility, verification, and recovery readiness as core pillars of supply chain risk management.
Pro tip: Pair continuous vendor monitoring with Veeam Data Platform’s secure backup and recovery capabilities to ensure that even if a supplier is compromised, you can restore quickly and keep operations moving.
Supply Chain Risk Management Best Practices
A resilient supply chain is the result of deliberate planning, continuous oversight, and a culture of accountability across your organization and vendors. Effective Supply Chain Risk Management (SCRM) requires both strategic and operational measures to protect against disruptions, whether caused by cyberattacks, operational failures, or compliance issues.
Below is a practical, actionable checklist you can use to strengthen your supply chain security posture:
1. Map Your Entire Supply Chain
- Create a detailed inventory of all suppliers, service providers, contractors, and technology vendors.
- Include not only direct suppliers but also fourth‑party and sub‑tier vendors that your partners rely on.
- Maintain a living document that’s updated as relationships change.
Why it matters: You can’t manage risks you don’t know exist. Mapping your chain ensures you have full visibility into potential vulnerabilities.
2. Classify Vendors by Criticality and Risk
- Identify which vendors provide essential products, services, or data access.
- Consider both operational criticality (impact on your ability to function) and security risk (likelihood of compromise).
- Apply stricter controls and monitoring to high‑risk vendors.
Why it matters: Risk prioritization focuses resources where they’ll have the greatest impact.
3. Conduct Thorough Due Diligence
- Evaluate vendor security policies, incident response procedures, and compliance certifications (e.g., ISO 27001, SOC 2, NIST frameworks).
- Review past security incidents and how they were handled.
- Ask for transparency on subcontractors and supply chain dependencies.
Why it matters: Trust is important, but verification is essential to avoid inheriting a vendor’s security weaknesses.
4. Establish Clear Security Requirements in Contracts
- Include clauses for data protection, breach notification timelines, encryption standards, and right‑to‑audit provisions.
- Require vendors to meet (or exceed) your organization’s security policies.
Why it matters: Written expectations set a baseline for accountability and give you leverage if the vendor fails to meet obligations.
5. Protect Critical Data with the Principle of Least Privilege
- Limit vendor access to only the data and systems they need to perform their work.
- Use segmentation and identity management to isolate sensitive environments.
Why it matters: Even if a vendor is compromised, restricted access reduces the potential blast radius.
6. Continuously Monitor Vendor Performance and Security Posture
- Implement ongoing risk assessments, not just annual reviews.
- Monitor for changes in financial stability, leadership, or operational capacity that could signal increased risk.
- Use threat intelligence to track vulnerabilities affecting your vendors’ industries.
Why it matters: Vendor risk is dynamic, so real‑time monitoring can help you detect and act on changes quickly.
7. Test Incident Response and Recovery Plans
- Run tabletop exercises simulating vendor outages or breaches.
- Ensure your team knows how to switch to backup suppliers or restore services from internally controlled systems.
- Document lessons learned and update plans accordingly.
- Have a working RACI (responsible, accountable, consulted, informed) chart to clearly define each team roles.
Why it matters: Preparedness reduces downtime and panic when a real incident occurs.
8. Stay Compliant with Relevant Regulations
- Know which laws and standards apply to your industry and geography (e.g., GDPR, NIS2, DORA, HIPAA).
- Ensure your vendors follow the same or higher compliance standards.
Why it matters: Regulatory penalties for vendor breaches can be costly, even if the incident originated outside your organization.
Pro tip: Treat supply chain risk management as a continuous cycle of identifying, assessing, mitigating, and monitoring. It’s not a one‑time project. Threats evolve, vendor relationships change, and new risks emerge constantly.
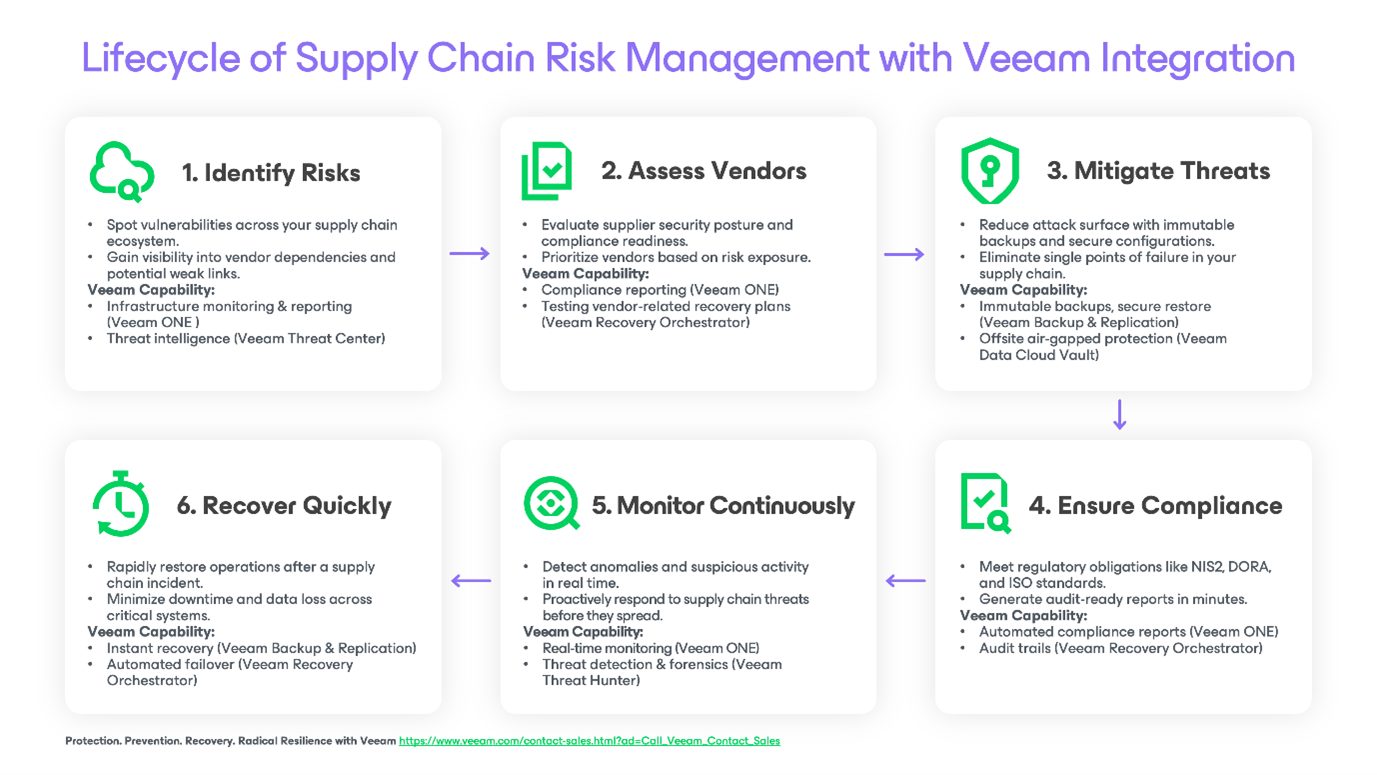
How Veeam Supports Supply Chain Risk Management
You can’t always control your suppliers’ security, but you can control how ready you are to respond when something goes wrong. Veeam’s approach to Supply Chain Risk Management centers on Data Resilience: the ability to protect, detect, and recover from any disruption, no matter where it originates.
Here’s how Veeam helps at every stage of the supply chain risk lifecycle:
1. Identify & Monitor Risks
- Veeam ONE delivers continuous monitoring and reporting across your data protection infrastructure, helping you detect anomalies that could indicate a third‑party compromise.
- Integration with security tools ensures you stay informed about emerging vendor vulnerabilities.
Benefit: You gain visibility into potential risks before they escalate into full‑blown incidents.
2. Protect & Isolate Critical Data
- Immutable backups by Veeam Backup & Replication ensure that even if a vendor’s system is compromised, your backup data cannot be altered or deleted.
- Air‑gapped and offsite storage options reduce the risk of a single point of failure across your supply chain.
Benefit: Your recovery data remains secure, even if attackers target your backup repositories.
3. Enable Fast, Verified Recovery
- Instant VM Recovery and granular restore options mean you can bring systems back online in minutes, bypassing compromised vendor systems if needed.
- SureBackup automatically verifies the recoverability of backups, so you know they’ll work before you need them.
Benefit: Minimize downtime and revenue loss when a supplier incident disrupts operations.
4. Maintain Compliance & Audit Readiness
- Built‑in reporting simplifies proof of compliance for regulations like GDPR, NIS2, and DORA.
- Detailed audit trails support vendor risk assessments and incident investigations.
- Measure and maintain secure backups and compliance with automated security best practices and compliance checks using tools like Veeam ONE, Veeam Security & Compliance Analyzer, and programs like Veeam Cyber Secure.
Benefit: Meet regulatory obligations with less manual effort and reduced audit stress.
5. Integrate with Your Existing Risk Strategy
- Veeam solutions work across hybrid and multicloud environments, integrating seamlessly with your existing supply chain monitoring and security tools.
- This ensures consistent protection, no matter where your data resides or how your supply chain evolves.
Benefit: You can extend resilience across your entire vendor ecosystem without adding operational complexity.
Build a Supply Chain That Can Withstand Anything
In today’s interconnected world, your security is only as strong as the weakest link in your supply chain. With the growing sophistication of supply chain cyberattacks, relying on prevention alone is no longer enough. You need the ability to detect issues early, respond decisively, and recover fast.
That’s what Radical Resilience with Veeam delivers. From immutable backups and instant recovery to continuous monitoring and compliance‑ready reporting, Veeam ensures you can protect your operations against disruptions, whether they stem from a malicious attack, a vendor outage, or a compliance failure.
Organizations that survive supply chain incidents are the ones that prepare, test, and invest in recovery‑ready infrastructure before disaster strikes.
Now is the time to strengthen your supply chain resilience — before you’re tested.
Related reading:
- Announcing Radical Resilience at VeeamON
- Ransomware Trends Report
- Veeam Data Platform
- Veeam Community: Data Platform Fundamentals
FAQs
1. What is supply chain risk management?
Supply chain risk management is the practice of identifying, assessing, and mitigating risks that could disrupt the flow of goods, services, or data across an organization’s supplier network, including operational, financial, and cybersecurity threats.
2. Why is supply chain risk management important for businesses today?
It’s critical because cyberattacks increasingly target vendors and service providers to infiltrate multiple organizations at once, making third‑party security weaknesses a major business risk.
3. What are the most common supply chain cyber risks?
Common risks include compromised software updates, insecure vendor access, ransomware via third‑party tools, data leaks from partners, and exploitation of unmanaged cloud services.
4. How does Veeam help strengthen supply chain resilience?
Veeam strengthens resilience with immutable backups, rapid recovery, and secure data protection across hybrid and multicloud environments. This includes the best threat detection capabilities for data resilience platforms in the market.
5. How is supply chain risk management different from general cybersecurity?
General cybersecurity focuses on internal systems and networks, while supply chain risk management extends protections to external vendors, partners, and third‑party dependencies that can impact your operations.
6. Can Veeam integrate with my existing risk management strategy?
Yes. Veeam integrates seamlessly with existing risk management frameworks, providing cross‑platform backup, recovery, and compliance reporting to enhance your overall security posture.
The post Supply Chain Risk Management: How Veeam Strengthens Your Resilience appeared first on Veeam Software Official Blog.
from Veeam Software Official Blog https://ift.tt/yZD4pqA
Share this content:
